
The Russian Alligator-class landing ship Saratov in the Bosporus in 2020.
The use of open source intelligence, which includes publicly available images and data, is resulting in real-time reporting on the war in Ukraine on an increasingly greater scale.
(Yoruk Isik)
The use of open source intelligence, which includes publicly available images and data, is resulting in real-time reporting on the war in Ukraine on an increasingly greater scale.
(Yoruk Isik)
From Stripes by Alison Bath
The Russian Alligator-class landing ship Saratov in the Bosporus in 2020.
The use of open source intelligence, which includes publicly available images and data, is resulting in real-time reporting on the war in Ukraine on an increasingly greater scale. (Yoruk Isik)
Citizen intelligence analysts are spotlighting the Russian navy’s role in its war on Ukraine, using publicly available information to report on missile launches, blockades and other actions in the Black and Mediterranean seas.
The information gathered using open-source intelligence, or OSINT, offers a glimpse into Russia’s maritime war activities and sometimes challenges information released by government sources.
Dozens of private citizens are parlaying their prior military experience, specialized knowledge of the Russian navy and online information-mining skills into robust, almost-real-time coverage of Russia’s full-scale invasion, which began Feb. 24.
Citizen intelligence analysts are spotlighting the Russian navy’s role in its war on Ukraine, using publicly available information to report on missile launches, blockades and other actions in the Black and Mediterranean seas.
The information gathered using open-source intelligence, or OSINT, offers a glimpse into Russia’s maritime war activities and sometimes challenges information released by government sources.
Dozens of private citizens are parlaying their prior military experience, specialized knowledge of the Russian navy and online information-mining skills into robust, almost-real-time coverage of Russia’s full-scale invasion, which began Feb. 24.
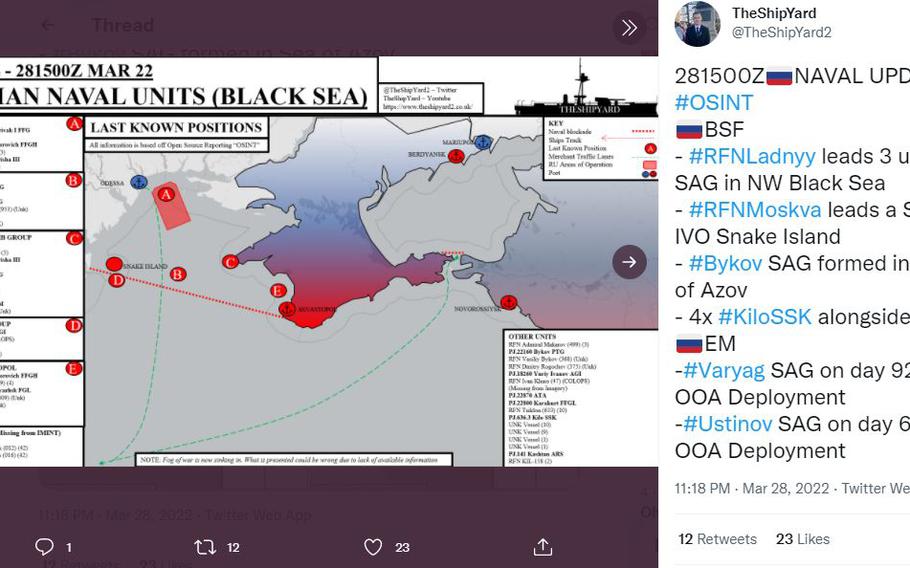
A map showing Russian naval units in the Black Sea on March 22, 2022.
The use of open source intelligence on Twitter and other social media platforms is resulting in real-time reporting on the war in Ukraine that sometimes challenges official narratives.
OSINT relies on public information such as satellite images, video and photographs, documents, databases, news stories and social media posts about a particular event or topic.
It’s painstaking work — usually unpaid — involving hourslong searches for information, verification of its authenticity and accuracy and then contextualization of events before analysis is posted on social media or a blog.
The work finds its roots in early government efforts by the U.S. and other countries to monitor news and other reports as part of intelligence gathering.
Not everyone has the skill set to parse the meaning of all this information, but those who do now have relatively easy access to satellite images and quality imagery recorded by increasingly sophisticated phones, experts say.
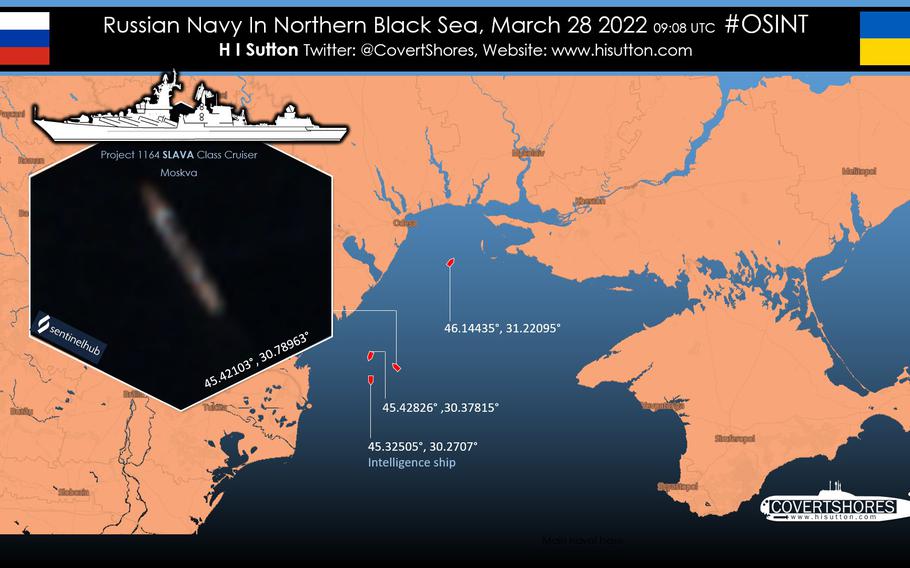
Open source intelligence provided by citizen analysts on Twitter and other social media forums is revealing Russia's full-scale war in Ukraine in minute detail.
“What I bring here is (professional) knowledge that I try to bring to open source using primary and secondary sources to actually give you an idea of what’s going on,” said James Phillips, a naval historian whose Twitter account, @TheShipYard2, presents detailed maps showing the location of Russian ships and other information.
On Monday, Phillips posted on Twitter a map showing an amphibious assault group in the Sea of Azov near the Ukrainian port city of Berdyansk.
In the early days of the invasion, images and public data gathered by private OSINT analysts painted a different picture of what an unnamed senior Pentagon official said was happening near the port city of Mariupol on the Sea of Azov.
The unidentified official indicated that a nighttime amphibious assault potentially involving thousands of Russian troops was underway there.
The assertion was tweeted out by several U.S. national security reporters and almost immediately challenged online.
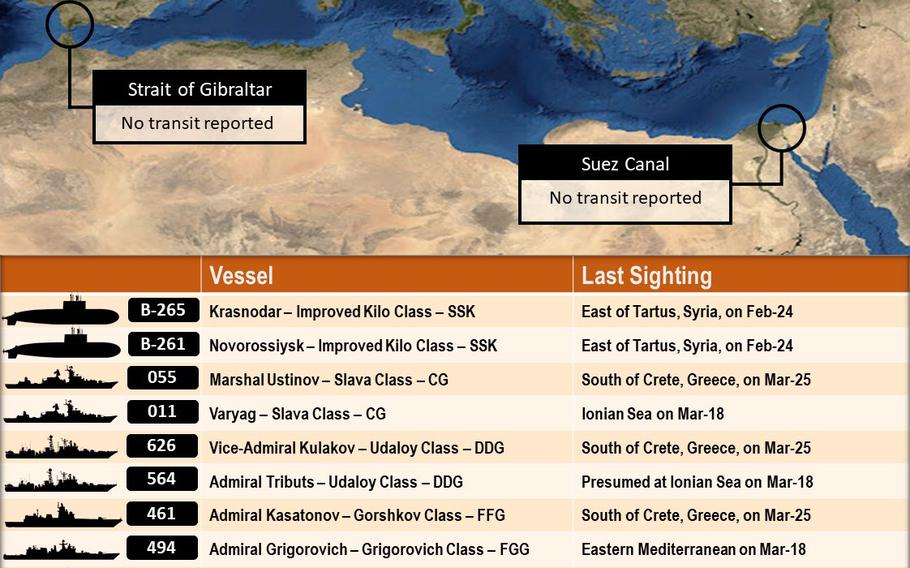
A list of Russia's naval deployment in the Mediterranean Sea compiled using open source intelligence by Frederik Van Lokeren, a former Belgian navy officer.
Van Lokeren is among several private citizens using their experience to provide detailed information online about the Russia-Ukraine war.
“I keep stressing: the Russian Navy never trained for night time amphibious assaults,” said Frederik Van Lokeren, a Belgian former navy officer, in a Feb. 26 tweet.
“They can not do this as they lack expertise and equipment needed. Why U.S. officials keep claiming otherwise for the second night in a row is beyond understanding.”
Van Lokeren's OSINT analysis found that a Russian amphibious assault group was in the Sea of Azov but he strongly disputed the number of sailors involved, which he estimated at 300 to 400 based on the number and size of the landing ships involved and their capacity.
He also expressed doubt that any naval landing had happened, citing a lack of evidence.
There were ample images in the days that followed of war damage and fighting in Ukraine, but none of a large-scale amphibious assault.
Van Lokeren's OSINT analysis found that a Russian amphibious assault group was in the Sea of Azov but he strongly disputed the number of sailors involved, which he estimated at 300 to 400 based on the number and size of the landing ships involved and their capacity.
He also expressed doubt that any naval landing had happened, citing a lack of evidence.
There were ample images in the days that followed of war damage and fighting in Ukraine, but none of a large-scale amphibious assault.
Read the latest from @TheStudyofWar and @criticalthreats:
In other cases, OSINT analysts were among the first to break news later addressed through official channels.
On Thursday, several analysts were quick to provide details on how a Russian Alligator-class landing ship in port in Berdyansk had caught fire, potentially as the result of a strike by a Ukrainian missile.
And on March 22, several analysts, including H. I. Sutton, who tweets as @CovertShores, posted video on Twitter showing a Russian ship near Sevastopol on the Crimean Peninsula firing eight Kalibr cruise missiles into Ukraine.
Others have kept running tallies on the last known locations of Russian navy ships, submarines and other vessels, detailing their actions in the Black and Azov seas and providing supporting information about capabilities and potential strategies.
On Thursday, several analysts were quick to provide details on how a Russian Alligator-class landing ship in port in Berdyansk had caught fire, potentially as the result of a strike by a Ukrainian missile.
And on March 22, several analysts, including H. I. Sutton, who tweets as @CovertShores, posted video on Twitter showing a Russian ship near Sevastopol on the Crimean Peninsula firing eight Kalibr cruise missiles into Ukraine.
Others have kept running tallies on the last known locations of Russian navy ships, submarines and other vessels, detailing their actions in the Black and Azov seas and providing supporting information about capabilities and potential strategies.
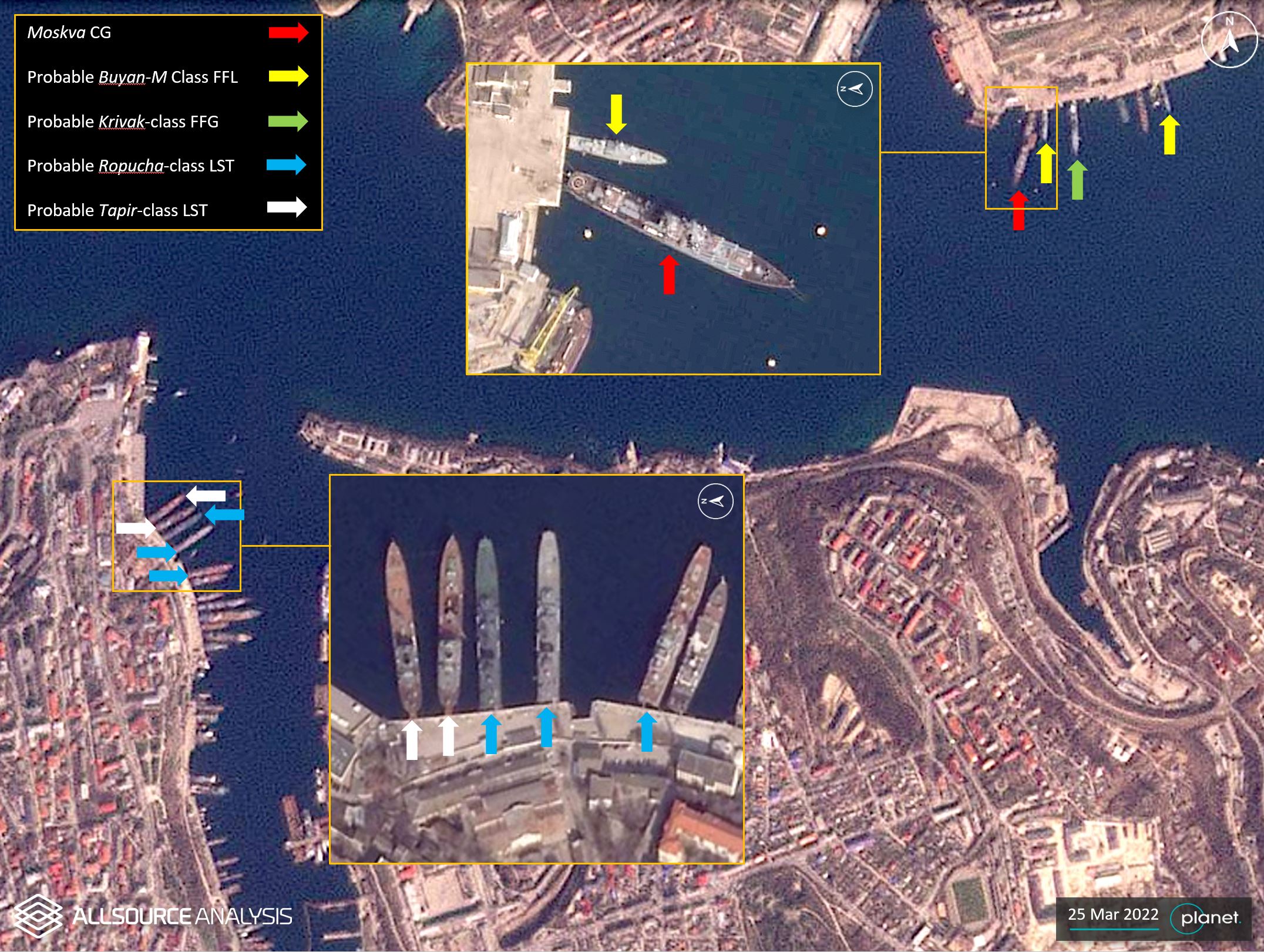
GEOINT analysis on 25 March 2022 shows several Russian naval vessels moored at the port of Sevastopol.
Russian navy vessels thought to be observing U.S. and NATO maritime activities in the eastern Mediterranean and protecting a Russian port in Tartus, Syria, also are analyzed.
“I haven’t seen a conflict this well-covered (through the OSINT community) in my career,” said Lukas Andriukaitis, associate director of the Digital Forensic Research Lab at the Atlantic Council think tank, in a phone interview.
“You can watch the conflict almost evolve live.”
There are signs that Moscow increasingly is aware of the OSINT community’s ability to quickly challenge narratives and document war crimes and other activities.
For example, before the war started, Russia took away troops’ cellphones, Andriukaitis said.
The Russian navy also recently started painting over ship numbers and obscuring other identifying information, Phillips and other analysts have noted.
The greatest contribution OSINT analysts have made came in the months leading up to the war, said Ryan Fedasiuk, an adjunct fellow for the Center for a New American Security’s technology and national security program.
The Russian navy also recently started painting over ship numbers and obscuring other identifying information, Phillips and other analysts have noted.
The greatest contribution OSINT analysts have made came in the months leading up to the war, said Ryan Fedasiuk, an adjunct fellow for the Center for a New American Security’s technology and national security program.
Interactive map of reports (with timestamps) about civilian casualties in Ukraine.
A private company publicized satellite images that correctly identified a buildup of nearly 200,000 Russian troops and advanced weaponry along the northern, eastern and southern borders of Ukraine.
Citizen journalists on Twitter also sounded the alarm bell in January that six Russian navy amphibious assault ships left the Baltic and North seas, passing through Gibraltar and into the eastern Mediterranean before entering the Black Sea.
The value of open-source intelligence is in sifting through the noise to identify signals that something is going to happen, he said.
“In the future, governments ought to take that sort of signal much more seriously, even if it isn’t a smoking gun, secretive indication of intent,” Fedasiuk said.
Links :
- BBC : How access to satellite images shifts the view of war
- The Conversation : Open-source intelligence: how digital sleuths are making their mark on the Ukraine war
- The Economist : The invasion of Ukraine is not the first social media war, but it is the most viral
- Time : How Open Source Intelligence Became the World's Window Into the Ukraine Invasion
- DALoop : Open-Source Intelligence Resources: The EU Disinformation Lab’s Ukraine Conflict Resource Hub
- SecurityBoulevard : Open Source Sabotage and Encryption Efficacy Emerge as Tactics in Ukraine Resistance
- GeoGarage blog : How companies are using AI to monitor sanctions risks on the Black Sea and beyond

No comments:
Post a Comment