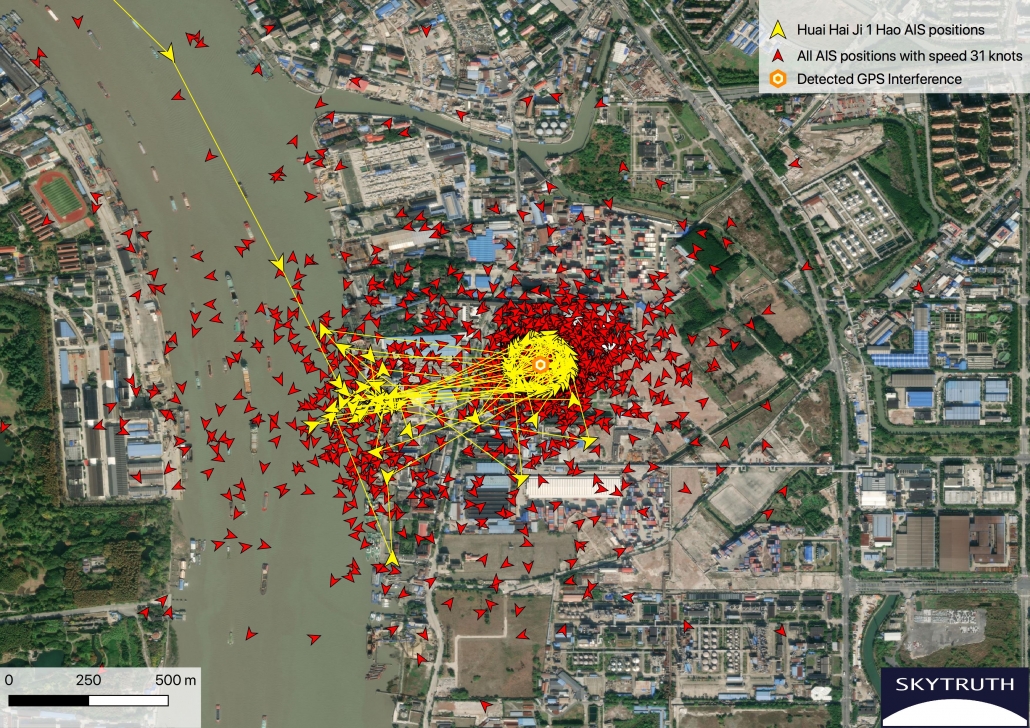
The Chinese cargo ship Huai Hia Ji 1 Hao (yellow) transits southeast on the Huangpu river.
Upon nearing the center of GPS interference area the track jumps to the ring on land and to other random positions nearby.
Positions from other affected vessels are shown in red.
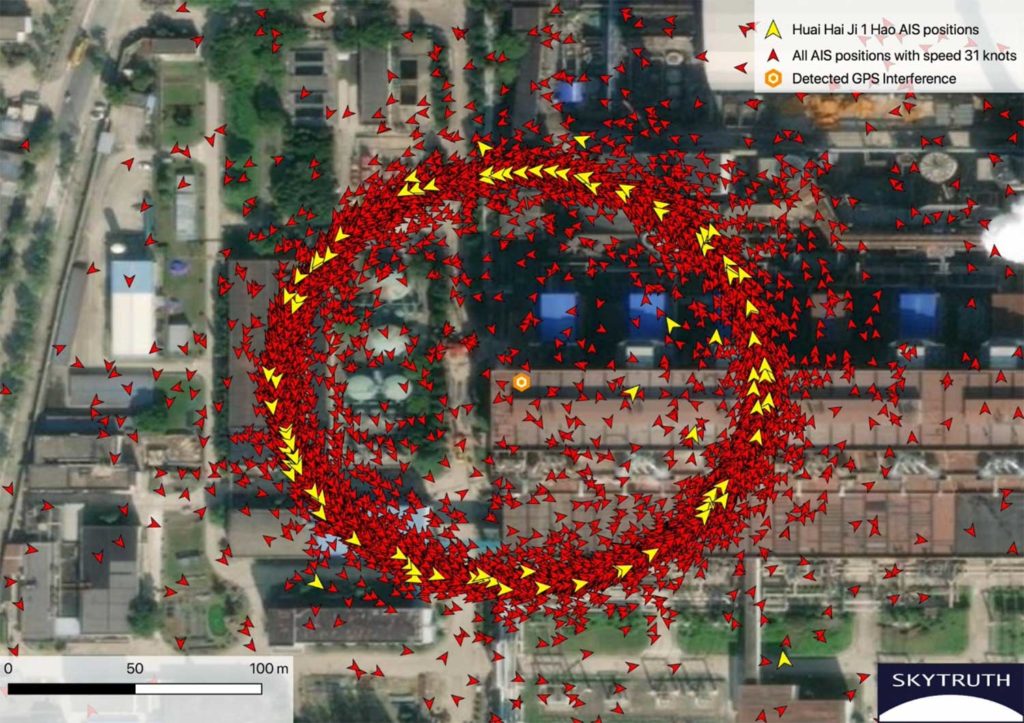
GPS interference can be pinpointed based on this ring of false AIS positions.
Approximately 200 meters in diameter, many of the positions in the ring had reported speeds near 31 knots (much faster than a normal vessel speed) and a course going counterclockwise around the circle.
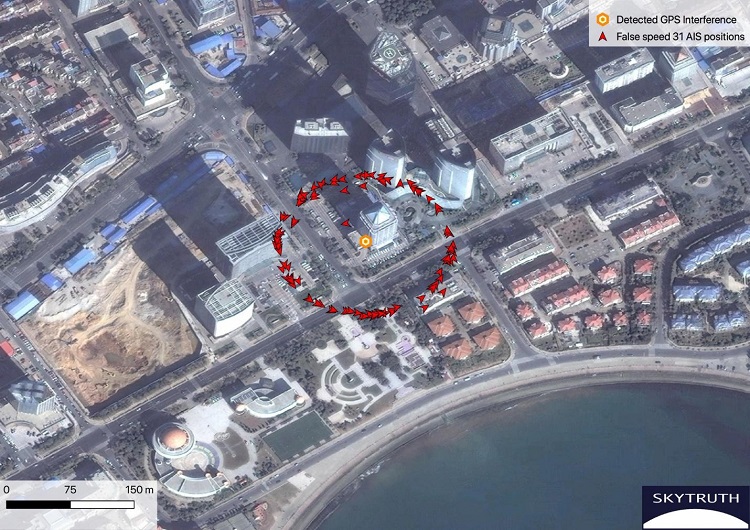
A ring of false AIS positions marks an apparent GPS interference device deployed in an office building identified as the Qingdao tax administration office.
AIS data courtesy Global Fishing Watch / Orbcomm / Spire.
From GPS World by Dana Goward
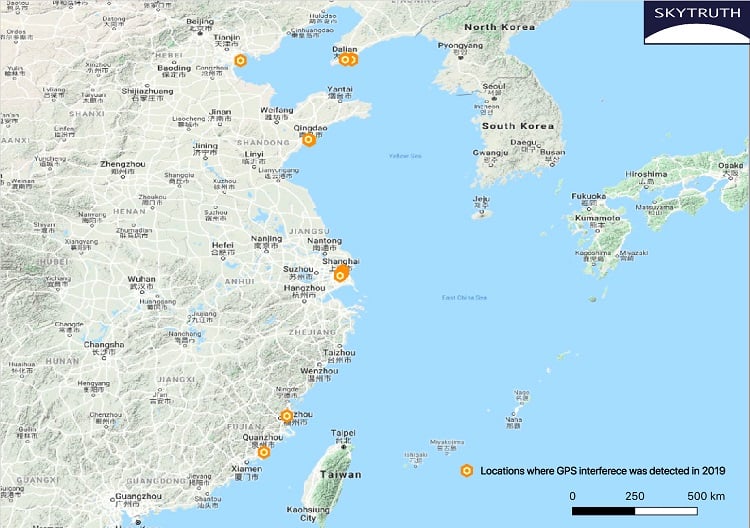
“GPS spoofing circles” have been discovered at 20 locations along the Chinese coast, according to the non-profit environmental group Skytruth.
Of the locations observed, 16 were oil terminals; the others were corporate and government offices.
GPS spoofing in Shanghai that resulted in reported positions from ships, fitness trackers and other GPS enabled devices forming circles some distance from the shore was first observed by the non-profit C4ADS.
Subsequently, Professor Todd Humphreys briefed the phenomena at an Institute of Navigation conference in September.
The MIT Technology Review published an article about it in November.
This caught the interest of an analyst at the environmental non-profit Skytruth.
Evaluating a larger data set of ship AIS (Automatic Identification System) data, analyst Bjorn Bergman discovered at least 20 locations near the Chinese coast where similar spoofing had taken place in the last two years.
Aggressive GPS spoofing impacting shipping has been detected in over 20 Chinese coastal sites during 2019. These included the ports of Shanghai, Fuzhou (Huilutou), Qingdao, Quanzhou (Shiyucun), Dalian, and Tianjin.
Sixteen of these “spoofing circle” locations were oil terminals.
The most frequent occurrences by far were at the port of Dalian in northern China, close to the border with North Korea.
Based upon the timing of the spoofing, imposition of sanctions on purchase of Iranian oil by the United States, and observations by others of Iranian oil being received by China, Bergman suggests that much of the spoofing is designed to help conceal these transactions.
Of the four locations not associated with oil terminals, three were government offices and one was the headquarters of the Qingjian industrial group, a huge engineering and construction conglomerate.
These infrequent and irregular events may be related to visits by important government officials.
A C4ADS report earlier this year demonstrated Russia uses GPS spoofing extensively for government VIP protection.
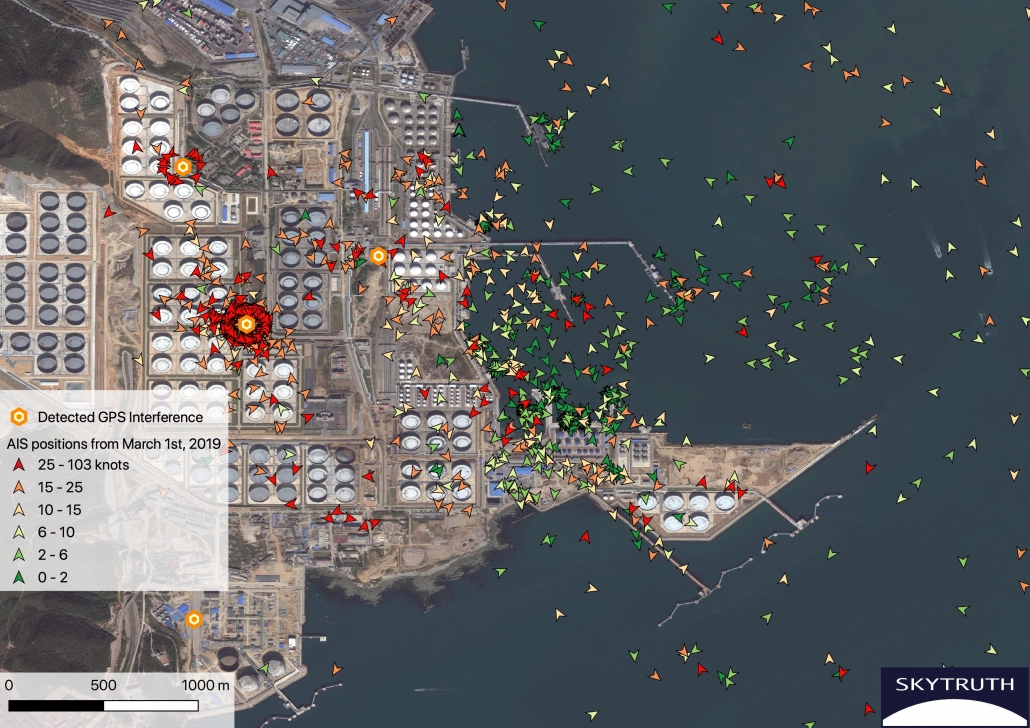
On March 1, 2019 AIS vessel position data around an oil terminal east of Dalian China shows accurate vessel positions and speeds.
On that date, none of the four locations of GPS interference were active.
Consequently no vessel positions appear on land and stationary vessels are accurately shown with near 0 speeds (green).
On September 5, 2019 two GPS interference locations were active and this had a dramatic effect on scrambling vessel positions in the area.
Many positions now appear orbiting the presumed GPS interference devices and others appear scattered on land.
On the water many positions are appearing with very high speeds (over 25 knots, red) and it’s not possible to distinguish true and false locations.
However some slow speed positions (green) are appearing at dock where they would be expected, so some AIS broadcasts appear to be unaffected.

The tanker Jin Niu Zuo approaches an oil terminal east of Dalian on September 5. Initially, positions with normal transit speeds appear (yellow).
With closer proximity, scattered high speed positions begin to emerge (red) and eventually most positions appear in the ring surrounding the presumed AIS interference device.
Bergman suggests that the actual spoofing device is located at the center of each of the rings formed by false GPS reports.
He has also observed that not all AIS/GPS receivers in the impacted area are affected, the spoofing circles tend to be about 200 meters in diameter, many false vessel positions orbit the circle counterclockwise at 21 knots or 31 knots, and some receivers are spoofed to locations other than the circle.
A new video showing how to spoof GPS from a Windows computer!
You don’t need to be a hacker (or know Linux) to spoof anymore. Scary.
"Note: I said 2.5ghz in the video but I meant 1.5Ghz for GPS signals. My antenna was 430mhz
Here we take a look at how to GPS Spoof with the HackRF SDR Transceiver.
Software used in this video:
https://github.com/osqzss/gps-sdr-sim
ftp://cddis.gsfc.nasa.gov/gnss/data/daily
https://downloads.myriadrf.org/builds...
Want to learn more about HackRF,
join the HackRF Facebook group: https://www.facebook.com/groups/hackRF/
Mass GPS spoofing is most easily detected and analyzed in coastal areas because of the availability of large data sets from AIS transmissions.
AIS is a maritime safety system that uses GPS for location and movement information.
This data is broadcast to other ships and shore stations to help prevent collisions and improve traffic management.
Close-up, Ship locations reported near Shanghai inner harbor, just before being spoofed.
Example of vessel traffic in Shangai
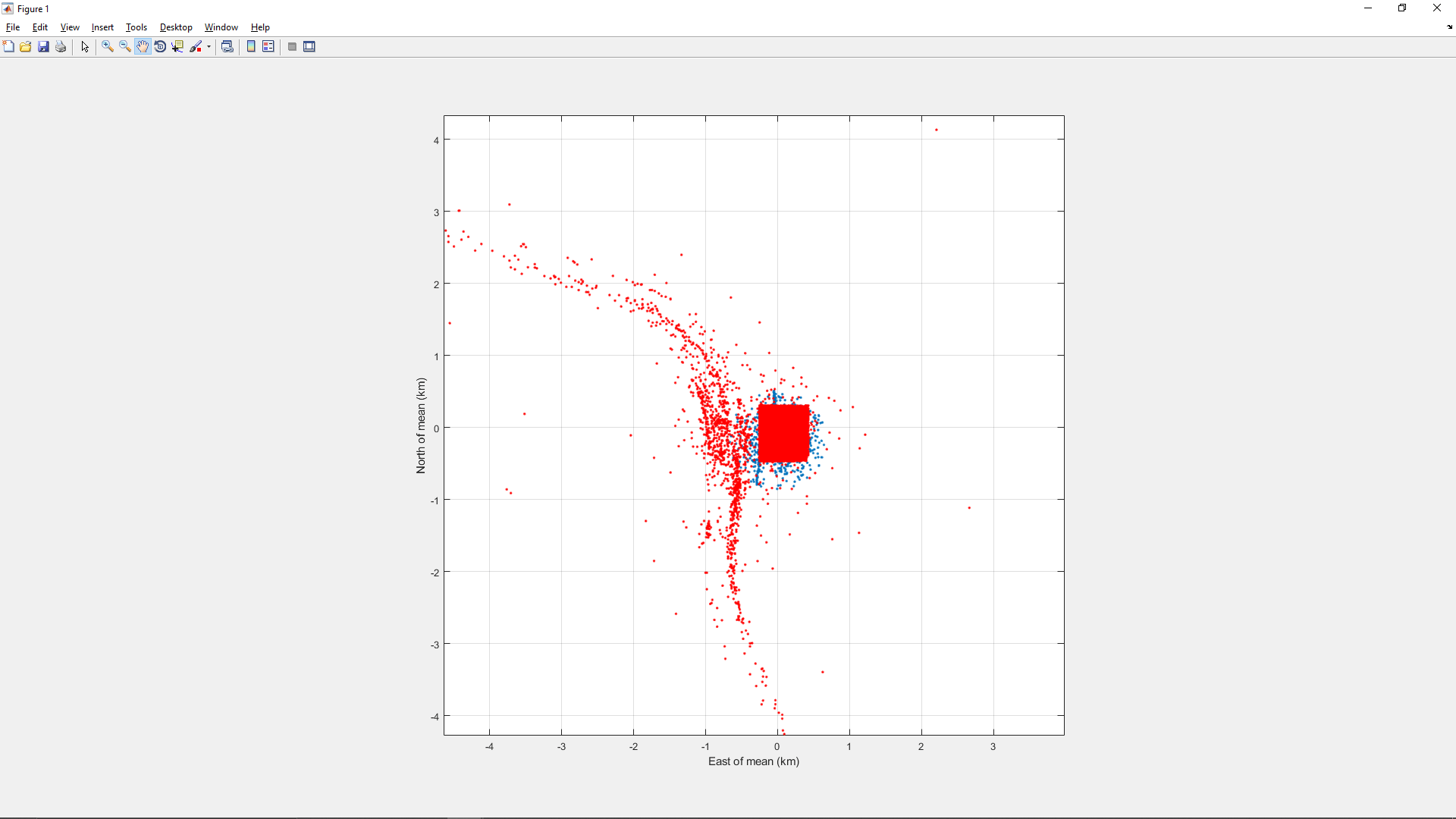
Here is an interesting plot of the locations ships reported just before being spoofed:
This indicates that the spoofing is affecting ships from the location of the circle all the way up the Huangpu to the Yangtze (about 10 km) and then along a stretch of the Yangtze that spans about 30 km.
This indicates that the spoofing is affecting ships from the location of the circle all the way up the Huangpu to the Yangtze (about 10 km) and then along a stretch of the Yangtze that spans about 30 km.
Affected ships are also found south of the circle for about 10 km along the Huangpu.
This view suggests that there is a higher density of prior-to-spoofed locations along the Huangpu just west of the bounding box.
This view suggests that there is a higher density of prior-to-spoofed locations along the Huangpu just west of the bounding box.
This may be due to a higher density of ships in that area, but given that the overall span of the first chart above is roughly centered on the bounding box, I think it’s safe to conclude that the higher density of prior-to-spoofed locations in the above chart indicates that the spoofer’s actual location is near the bounding box (and thus near the circle).
Image: Todd Humphreys
The U.S. Coast Guard first experimented with receiving AIS signals by satellite in 2008.
Since that time, numerous governments and commercial entities have established AIS data services using both space-based and terrestrial receivers.
It is likely that the kinds of disruptions seen in Russian and Chinese maritime regions are occurring elsewhere.
The lack of easily accessible data from non-maritime areas, though, makes this more difficult to detect.
Confounding this problem is an apparent reluctance of many users to report disruptions.
The U.S. Coast Guard Navigation Center has had only one official report a GPS problem from a user in Russian waters and one from Chinese waters, for example.
Yet it is clear that thousands of vessels have been impacted in ways that must have been quite evident to their captains and crews.
Links :
- Maritime Exceutive : Patterns of GPS Spoofing at Chinese Ports
- Inside GNSS : Sinister Spoofing in Shanghai
- TechRadar : This Android VPN is now able to disguise your GPS location
- NoJitter : Understanding GPS Data Spoofing
- GPS World Mag : Access denied: Anti-jam technology mitigates navigation ... / How do we ensure GNSS security against spoofing?
- Ars Technica : Preventing GPS spoofing is hard—but you can at least detect it
- Pulse / ZDnet : GPS inventor: We need to fix GPS's jamming problem - ZDNet
- The Drive : New Type Of GPS Spoofing Attack In China Creates "Crop Circles" Of False Location Data
- GeoGarage blog : Ghost ships, crop circles, and soft gold: A GPS mystery in Shanghai



SpaceNews : New studies show growing proliferation of anti-satellite weapons
ReplyDelete