GPS constellation
From DirectionsMag by Diana S. Sinton
The most ubiquitous way that the world intersects with the geospatial domain is through location-enabling technologies such as GPS and other GNSS that power and support transportation, communication, and logistics around the globe.
This component of our invisible infrastructure is deeply embedded into our daily lives in ways we usually don’t think about, apart from when we expect our ability to navigate to be accurate and instantaneously available.
Undermining the systems’ reliability? Messing with the GPS? Them’s fightin’ words.
Still, it’s happening and more frequently.
The 30 or so GPS satellites themselves are not as vulnerable to disruption as the signals that they send out and the units that receive them.
For instance, it might seem like a nice idea to create a quiet zone by having incoming calls, messages, and Wi-Fi blocked in an area, but jamming these signals puts many other systems – like GPS – at collateral risk.
It’s illegal to own, sell, or use a GPS jammer in the United States but that’s not so in many other places.
The devices themselves are produced in large quantities in China and elsewhere, and their low cost (about $100 or less) makes them even more tempting for malfeasants.
Where there’s a will, there’s a way for people to acquire and use these.
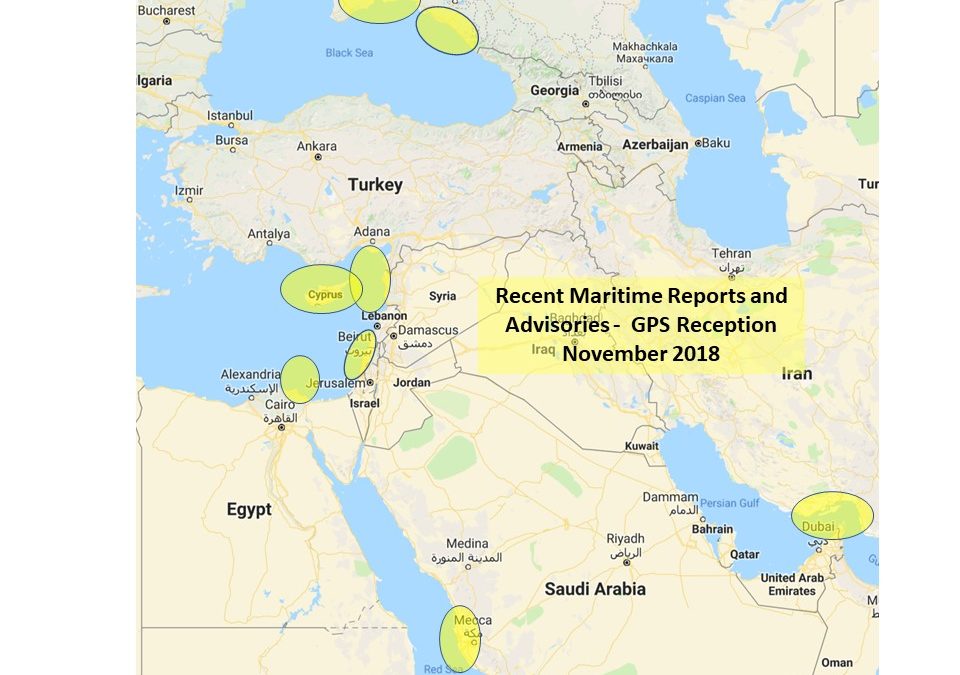
Maritime GPS disruptions have been reported elsewhere, but seem to be particularly common in this part of the world.
Electronic
navigation signals from the Saudi Arabian Loran-C system and the
Russian Chayka/Loran-C system are available for use across most of this
region.
Jamming signals is the simple, but less elegant, approach to GPS signal disruption.
Its more complicated and more sophisticated cousin, GPS spoofing, is also becoming more accessible, both technically and financially.
Spoofing works by sending fake signals to a GPS receiver that mimic the ones that the real satellites send.
Weak signal strength of these false ones was a problem in the past, but new technologies have allowed the signals to become strong enough – and more similar to the real ones – that it is possible to have the receiver begin to follow the false ones over the real ones.
As David Last, a former president of the United Kingdom’s Royal Institute of Navigation, recently said, “Jamming just causes the receiver to die, spoofing causes the receiver to lie.”
Todd Humphries, an engineering professor at the University of Texas at Austin, explains it well in his 2012 TEDx presentation.
In the video he shares footage of how he has made the little blinking blue dot on his cell phone’s map – the universal icon for the “you are here” symbol – start to drift blocks away from his home location where he and his phone are actually sitting still.
Since then, he and his research team have done more than these simple at-home demonstrations.
In 2013, they tested their spoofing technologies on a 200-foot yacht in the Mediterranean (with the full cooperation and awareness of the ship’s crew) and digitally manipulated the ship to adjust its directional course as a “correction” that was in fact a complete misdirection.
The ship’s autopilot simply followed its own protocols to make the adjustment, without any awareness that the incoming signals were bogus.
Reports of satellite navigation problems in the Black Sea
suggest that Russia may be testing a new system for spoofing GPS.
source : NewScientist
Larger ships are just as vulnerable to these manipulations.
In 2017, a tanker ship in the Black Sea had its navigational system indicate that it was suddenly in a completely different and improbable location: at an airport 30 kilometers away from its actual location at sea.
All together about 20 ships were affected by this temporary attack, which is now believed to have been Russians experimenting with new approaches to cybersecurity breaches.
GPS signals are regularly jammed in areas immediately around the Kremlin in Moscow, but this Black Sea trouble was the largest real and successful spoofing effort known to date.
Some GPS spoofers have more innocuous intentions, such as those who would try to fool their fellow Pokémon GO players by faking movements.
But really, there are more ways to cause harm than good with these abilities.
Virginia Tech’s Curtis Zeng and his colleagues have managed to further lower the barriers by creating a successful spoofing system that costs only a few hundred dollars.
With this inexpensive system in place, they were able to insert manipulated, false signals into navigational routes that were being followed by volunteers in a simulated driving situation.
The attacker does not change the original destination, but instead manipulates the user's real-time location (now a “ghost” location) on the map.
The navigation system will recalculate a fake virtual route from the ghost location to the original destination, one that would be physically feasible for the user to travel in the real world.
Ideally, this would not trigger the telltale "re-calculating" warning, depending on whether the ghost location is on or off the original navigation route.
Drivers continue to follow the navigation instructions, but now they are actually on a new route that the attackers planned.
Even more tricky is that Zeng and his colleagues managed to swap in false map layouts to further keep the drivers in the dark.
With these “ghost” maps in place, almost all of the drivers in this study naively continued to follow directions that had been tweaked to arrive at false destinations.
According to Zeng, “Users tend to heavily rely on navigation systems in unfamiliar areas rather than learning the map and planning routes ahead in an old-fashioned way.
It is (already) hard for them to drive, follow navigation instructions, and cross-check the surrounding environment at the same time.
Moreover, few users understand how navigation systems work and how hackers can manipulate them.
Many users have also experienced brief navigation malfunctioning in real life, so a rapid ‘blip’ in the system does not alert them (to any changes having been made).”
Tech-smart people are figuring out how to do this for nefarious reasons and other tech-smart people are working to stop them, or at least give us more chances for better outcomes.
A group of Irish electrical engineers recently documented the ways in which they could successfully achieve multi-frequency spoofed GPS signals with inexpensive and readily available equipment, to show that it could be done (multi-frequency had been thought unachievable) and to continue to keep the conversations active.
Overestimating and underestimating the capacities of the adversaries are both counterproductive activities.
Hacking ships
Efforts with multiple strategies and tactics are underway by researchers, the public sector, and the federal government to combat the problems.
What several of these have in common is that they’re working to have the overall system of navigation be less reliant on GPS signals and their related time stamps alone.
Those atomic-clock-enabled time stamps are considered so reliable that they are counted on for countless processes.
At Clemson University, engineers are experimenting with a technique that regularly samples real GPS signals and tags those signals in a way that confirms their validity.
Other users’ devices can automatically compare the ones issued by Clemson with the ones that their devices are collecting.
This isn’t stopping spoofing from happening, but it is making the end user aware if their signals are being compromised.
Meanwhile, other researchers are taking it a step further and developing ways to correct the compromised signals.
Other approaches being pursued by private companies involve having navigational systems ready to receive signals from alternative sensors, such as mobile phone networks or commercial satellites, when it is detected that the GPS signals have irregularities.
These diverse strategies may not seem coordinated, but one organization that is staying on top of the problem is the Resilient Navigation and Timing Foundation, a group that is involved with the situation on many global fronts.
We’re confronted with jamming and spoofing that can be accomplished successfully by small-time actors building cheap contraptions in their basements, and larger actors, with deeper pockets and expertise, that may be working on behalf of foreign governments.
Really, it’s all part of a bigger problem: that the whole GPS system has too few redundancies and too many potential leaks that can be compromised too readily.
One path being pursued is simply to have more GPS satellites be part of the collection as quickly as possible, and to produce new receivers designed with as many cybersecurity countermeasures as possible.
We celebrate the open GPS system that provides us with such novel and independent ways to leverage location-based goods and services, but it’s clearly been a mixed blessing.
Links :
- RNTFND : GPS disrupted for maritime in Mediterranean, Red Sea
- MARAD Advisory
- The Independent : Russia 'deliberately disrupted GPS signals during Nato drill'
- WashingtonPost : Norway says Russia jammed GPS signal during NATO drill
- Business Insider : Finland says its GPS was disrupted during NATO's biggest war games ...
- BarentsObserver : Pilots warned of jamming in Finnmark / Moscow says Norway’s accusations about GPS jamming are «absurd»
- AtlanticCouncil : Electronic Jamming Between Russia and NATO is Par for the Course in the Future, But it Has its Risky Limits
- CNN : GPS jamming raises more alarms
- SputnikNews : Russia sinks Norwegian frigate (?)
- BreakingDefense : Russians Tried to Jam NATO Exercise; Swedes Say They’ve Seen This Before
- MarineCorpsTimes : Here’s why Marine Raiders want to take down GPS, cellphones and a Russian navigation service
- CTS Technology : Handheld digital drone jammer block all kinds of uav ISM, HAM, and GNSS GPS and GLONASS 1500M jamming range
- GeoGarage blog : Mass GPS spoofing attack in Black Sea? / Superyacht GPS spoofing experiment on the high seas / Why it's not surprising that ship collisions still happen / Hacking, tracking, stealing and sinking ships / Opinion: Were US sailors 'spoofed' into Iranian ... / Enhanced maritime situational awareness with ... / Rising fraud in the high seas / Cyber threats prompt return of radio for ship navigation / Combatting maritime cyber security threats / Cybercrime on the high seas: the new threat facing ... / Hacked at Sea: Concerns grow over lax ... / GPS back-up: World War Two technology employed / Nightmare scenario: ship critical systems easy target ... / Maritime Traffic Alert and Collision Avoidance ... / Relying on GPS could leave you lost at sea / New Air Force satellites launched to improve GPS / Navigational backup to aid ships in Dover straits / Sat-nav systems under growing threats


No comments:
Post a Comment